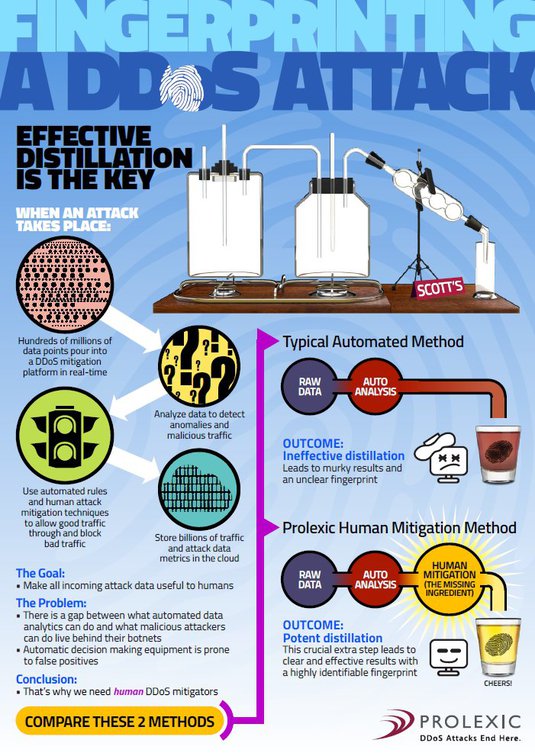
Hundreds of millions of data points pour into a DDoS mitigation platform in real-time. Prolexic’s human mitigation method allows for potent distillation for clear and effective results with a highly identifiable attack fingerprint.
This DDoS mitigation infographic reveals: • When a DDoS attack takes place hundreds of millions of data points pour into a DDoS mitigation platform in real-time • The DDoS mitigation service decides which network traffic to let through and which to block • To make this decision, the DDoS mitigation service must find answers to a complex set of preliminary questions about the data • The DDoS mitigation service stores billions of attack metrics in data centers and the cloud • The goal is to make all incoming attack data useful to humans • The problem is that there is a gap between what automated data analytics can do and what malicious actors can do live behind their botnets • Unfortunately, automatic decision making equipment is prone to false positives • Typical automated data analysis methods lead to murky results and an unclear fingerprint • The Prolexic human DDoS mitigation method is a crucial extra step that leads to clear and effective results with a highly identifiable attack fingerprint http://www.prolexic.com/knowledge-center-fingerprinting-a-ddos-attack-data-analytics-infographic.html?cvosrc=3rd |
|


